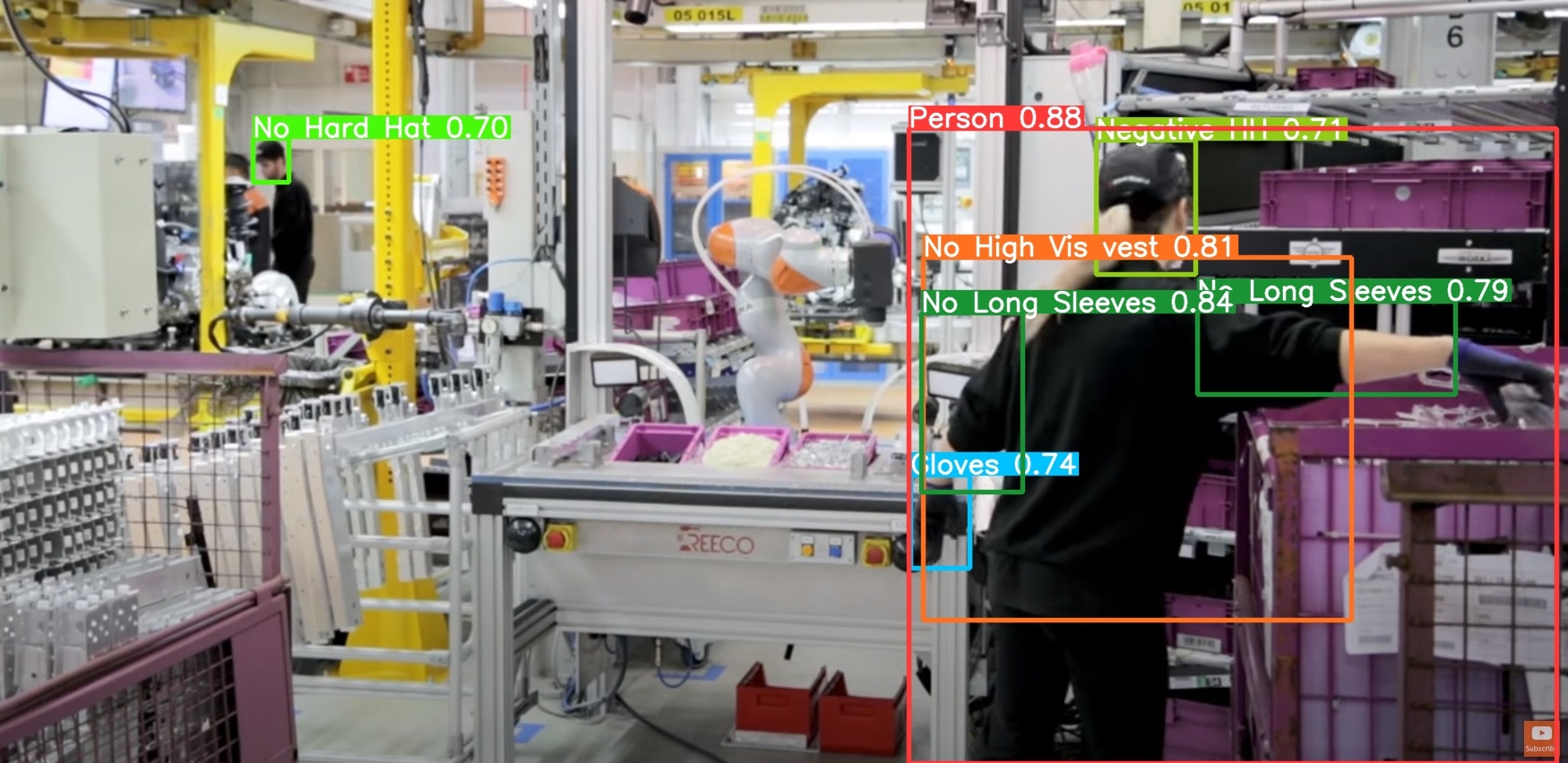
Nokia portfolio of industrial applications and devices
Select based on your needs/requirements
Featured applications and devices
Featured Devices
Portfolio
Product type
Device Categories
Industry Segments
Technologies
Certifications
-
Image

Crosser
Short descriptionIIoT edge platform
Connect, integrate and analyze operational data in real-time to provide many industrial use cases. Real-time streaming analytics and integration with automated workflows, low code development and the ability to bring your own algorithm capabilities enables many industrial use cases. Connect to 800+ industry systems with pre-built connectors for edge to cloud data flows and pipelines and facilitate digital twins by creating live loops of streaming data between connected devices and cloud for applications such as condition monitoring.
Manufacturer Manufacturer
Manufacturer Image
Image
Crosser
Short descriptionIIoT edge platform
Connect, integrate and analyze operational data in real-time to provide many industrial use cases. Real-time streaming analytics and integration with automated workflows, low code development and the ability to bring your own algorithm capabilities enables many industrial use cases. Connect to 800+ industry systems with pre-built connectors for edge to cloud data flows and pipelines and facilitate digital twins by creating live loops of streaming data between connected devices and cloud for applications such as condition monitoring.
-
Image

Litmus
Short descriptionIIoT edge platform
Put data to work for operations to transform at scale. Litmus, the Industrial EdgeOps platform that Unlocks.Activates.Scales. Litmus unifies data collection, normalization, contextualization, and analytics at the edge and cloud. Litmus unlocks intelligence to improve efficiency, profitability and security. Nearly 300 pre-built device drivers and integrations for OT assets and enterprise systems, along with digital twin and machine learning models, make it easier to address asset monitoring, anomaly detection, energy consumption, forecasting, predictive maintenance and more.
Manufacturer Manufacturer
Manufacturer Image
Image
Litmus
Short descriptionIIoT edge platform
Put data to work for operations to transform at scale. Litmus, the Industrial EdgeOps platform that Unlocks.Activates.Scales. Litmus unifies data collection, normalization, contextualization, and analytics at the edge and cloud. Litmus unlocks intelligence to improve efficiency, profitability and security. Nearly 300 pre-built device drivers and integrations for OT assets and enterprise systems, along with digital twin and machine learning models, make it easier to address asset monitoring, anomaly detection, energy consumption, forecasting, predictive maintenance and more.
-
Image

OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
Manufacturer Manufacturer
Manufacturer Image
Image
OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
-
Image

Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
Manufacturer Manufacturer
Manufacturer Image
Image
Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
-
Image

Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Manufacturer Manufacturer
Manufacturer Image
Image
Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
-
Image
Siemens MindConnect Software Agent
Short descriptionUnlock the potential of IIoT data
Unlock the potential of IIoT data for use by industrial applications. Enable fast, seamless connection to operational data and assets and make it available to Siemens Insight Hub, an integral part of the new Siemens Xcelerator portfolio, for analytics and applications.
Manufacturer Manufacturer
Manufacturer Image
Image
Siemens MindConnect Software Agent
Short descriptionUnlock the potential of IIoT data
Unlock the potential of IIoT data for use by industrial applications. Enable fast, seamless connection to operational data and assets and make it available to Siemens Insight Hub, an integral part of the new Siemens Xcelerator portfolio, for analytics and applications.
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.