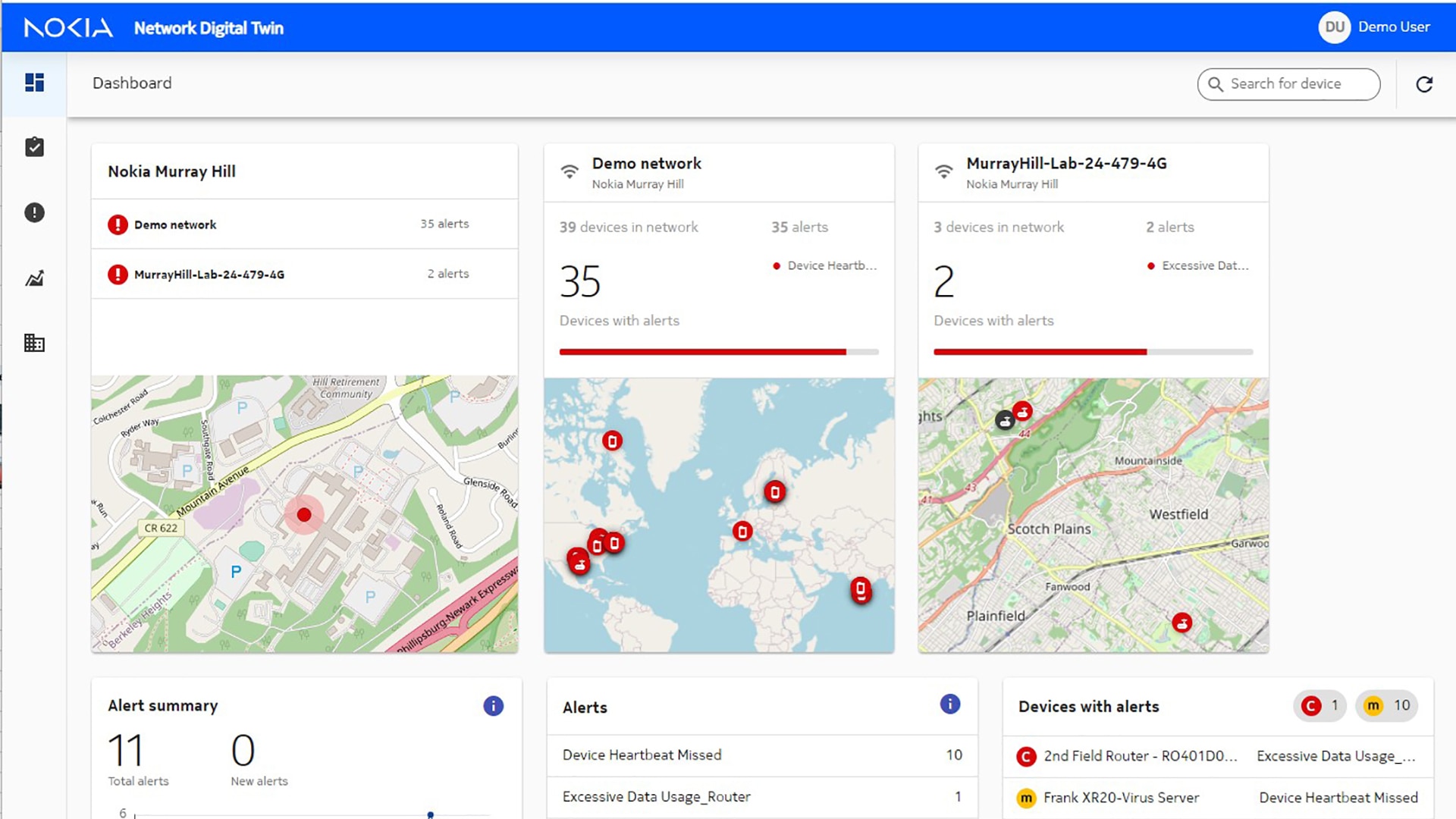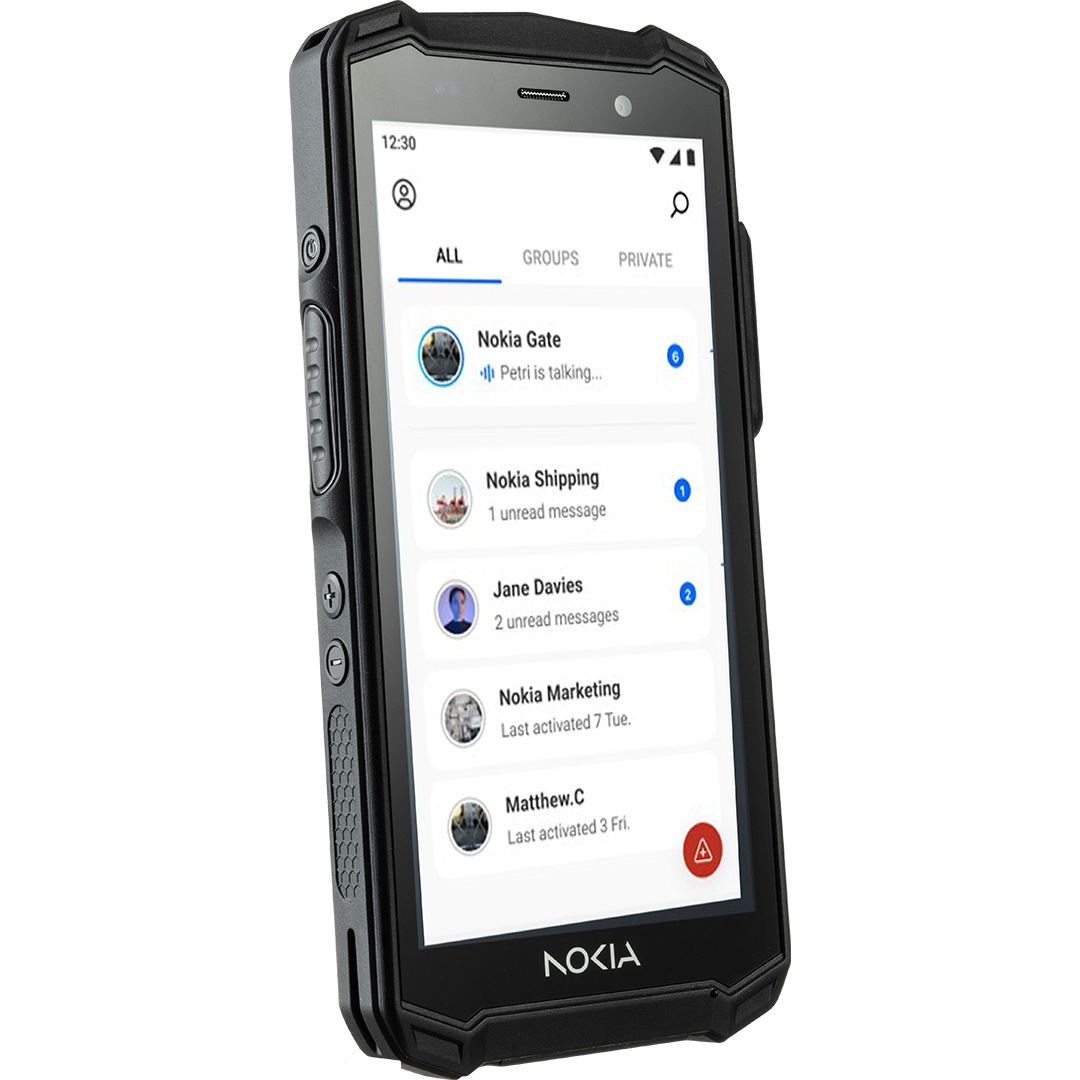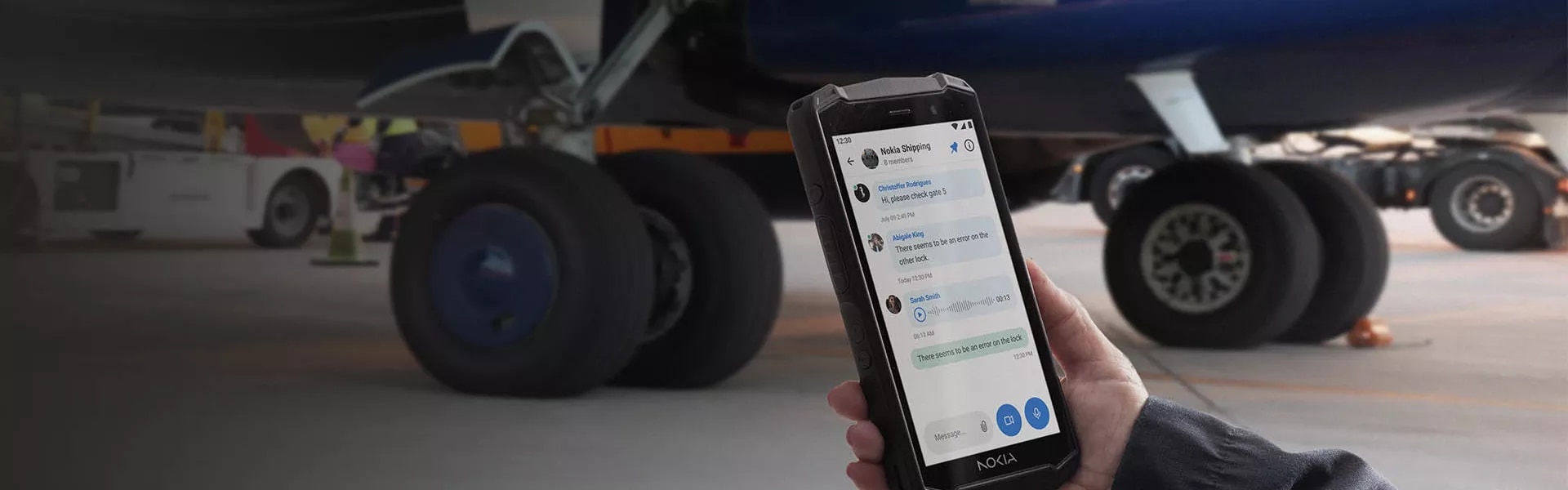
Nokia portfolio of industrial applications and devices
Select based on your needs/requirements
Featured applications and devices
Featured applications
Featured Devices
Portfolio
Product type
Device Categories
Industry Segments
- (-) Applicable to most industries
- Airports & Aviation
- Automotive & highways
- Communication Service Provider
- Defense
- Education
- Healthcare
- Hospitality
- Logistics
- Manufacturing
- Mining
- Oil and Gas
- Public Safety
- (-) Railways
- Renewables
- Seaports & Maritime
- Smart cities
- Systems Integrator
- Utilities
- Webscale
Technologies
Certifications
-
Image

Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
Manufacturer Manufacturer
Manufacturer Image
Image
Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
-
Image

Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Manufacturer Manufacturer
Manufacturer Image
Image
Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.