Nokia portfolio of industrial applications and devices
Select based on your needs/requirements
Featured applications and devices
Featured applications
Featured Devices
Portfolio
Product type
Application Categories
Device Categories
Usage
- Call and send messages
- Connect data
- Connect machines
- Connect workers
- Deploy for devices
- Extend your reality (XR, VR)
- Find and track
- Improve efficiency
- Improve enterprise security
- Improve device usability
- Improve productivity
- Improve worker safety
- Improve security
- Improve situational awareness
- Manage devices
- Monitor networks
- Support industrial protocols
- Use in hazardous environments
- Video communication / Visual data transmission
- Other
Industry Segments
- Applicable to most industries
- Agriculture
- Airports & Aviation
- Automotive & highways
- Communication Service Provider
- Defense
- Education
- Government
- Healthcare
- Hospitality
- Logistics
- Manufacturing
- Mining
- Oil and Gas
- Public Safety
- Railways
- Renewables
- Seaports & Maritime
- Smart cities
- Systems Integrator
- Utilities
- Webscale
Technologies
-
Image

Nordic ID
Short descriptionRFID tracking solution providing every item a digital identity
Get a complete solution including hardware and software to track high velocity goods throughout the supply chain. Nordic ID comes with barcode scanning, RFID and Platform as a Service solutions. RFID, BARCORDE readers, including fixed and handheld devices. It is a single interface for all reader data. Middleware is sensor independent and can store all kinds of sensor data such as RFID, QR codes, barcodes, Bluetooth and RFID sensor data and pictures. Automatic inventory management with set limit alerts. Real time asset tracking providing product location, usage, hours, calibration time, alarms.
Manufacturer Manufacturer
Manufacturer Image
Image
Nordic ID
Short descriptionRFID tracking solution providing every item a digital identity
Get a complete solution including hardware and software to track high velocity goods throughout the supply chain. Nordic ID comes with barcode scanning, RFID and Platform as a Service solutions. RFID, BARCORDE readers, including fixed and handheld devices. It is a single interface for all reader data. Middleware is sensor independent and can store all kinds of sensor data such as RFID, QR codes, barcodes, Bluetooth and RFID sensor data and pictures. Automatic inventory management with set limit alerts. Real time asset tracking providing product location, usage, hours, calibration time, alarms.
-
Image

Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
Manufacturer Manufacturer
Manufacturer Image
Image
Nozomi Guardian
Short descriptionOT/IIoT asset vulnerability management, threat detection and response
Nozomi Guardian is an operational technology (OT) cybersecurity platform that provides real-time out of band IIoT asset visibility, threat detection and vulnerability identification for critical infrastructure for manufacturing and other industry verticals.
-
Image

OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
Manufacturer Manufacturer
Manufacturer Image
Image
OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
-
Image

Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
Manufacturer Manufacturer
Manufacturer Image
Image
Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
-
Image

Palo Alto Networks NGFW PA-410R-5G
Short descriptionThe PA-410R-5G is a ruggedized, IP65 rated firewall built for industrial, commercial, and government use in extreme environments. It features 5G connectivity with dual SIM support, multiple ports for reliable networking, and a fanless, compact design for flexible installation.
Manufacturer Manufacturer
Manufacturer
-
Image

Palo Alto Networks NGFW PA-450R-5G
Short descriptionThe PA-450R-5G is a ruggedized, machine-learning-powered next-generation firewall (NGFW) designed for industrial, commercial, and government deployments requiring wireless connectivity. Engineered for harsh environments, it withstands extreme temperatures and high humidity, ensuring reliable performance in demanding conditions.
Manufacturer Manufacturer
Manufacturer
-
Image
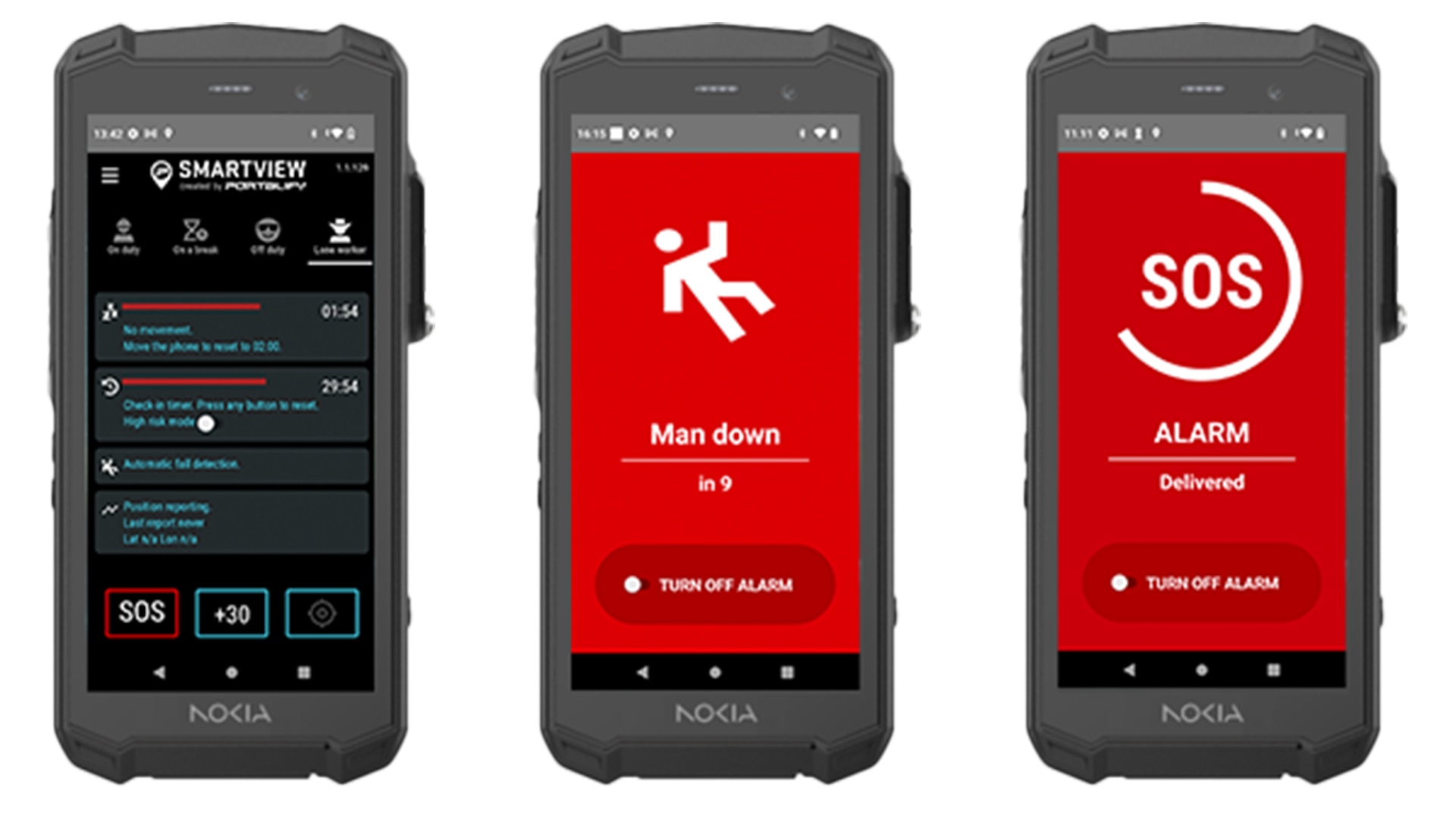
Portalify SmartView
Short descriptionOutdoor and indoor location tracking and alerts for smartphones
Provides operational teams with indoor and outdoor location tracking for workers using smartphones and other tracking and positioning technologies with a focus on lone worker requirements, like man-down. In case of an emergency, workers can raise alerts and worker location can be shared with operational teams and coworkers to accelerate response. Control room map view shows worker safety emergencies, indoor and outdoor location and work status information.
Manufacturer Manufacturer
Manufacturer Image
Image
Portalify SmartView
Short descriptionOutdoor and indoor location tracking and alerts for smartphones
Provides operational teams with indoor and outdoor location tracking for workers using smartphones and other tracking and positioning technologies with a focus on lone worker requirements, like man-down. In case of an emergency, workers can raise alerts and worker location can be shared with operational teams and coworkers to accelerate response. Control room map view shows worker safety emergencies, indoor and outdoor location and work status information.
-
Image

Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Manufacturer Manufacturer
Manufacturer Image
Image
Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
-
Image

Remote speaker microphones and headsets
Short descriptionTo ensure worker safety and improve Nokia Industrial device usability and ergonomics, we offer accessories that allow you to keep your protective gear on while communicating easily and efficiently. No need to take your gloves off! You can make and receive phone calls and engage through push-to-X communication.
Manufacturer Manufacturer
Manufacturer
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.