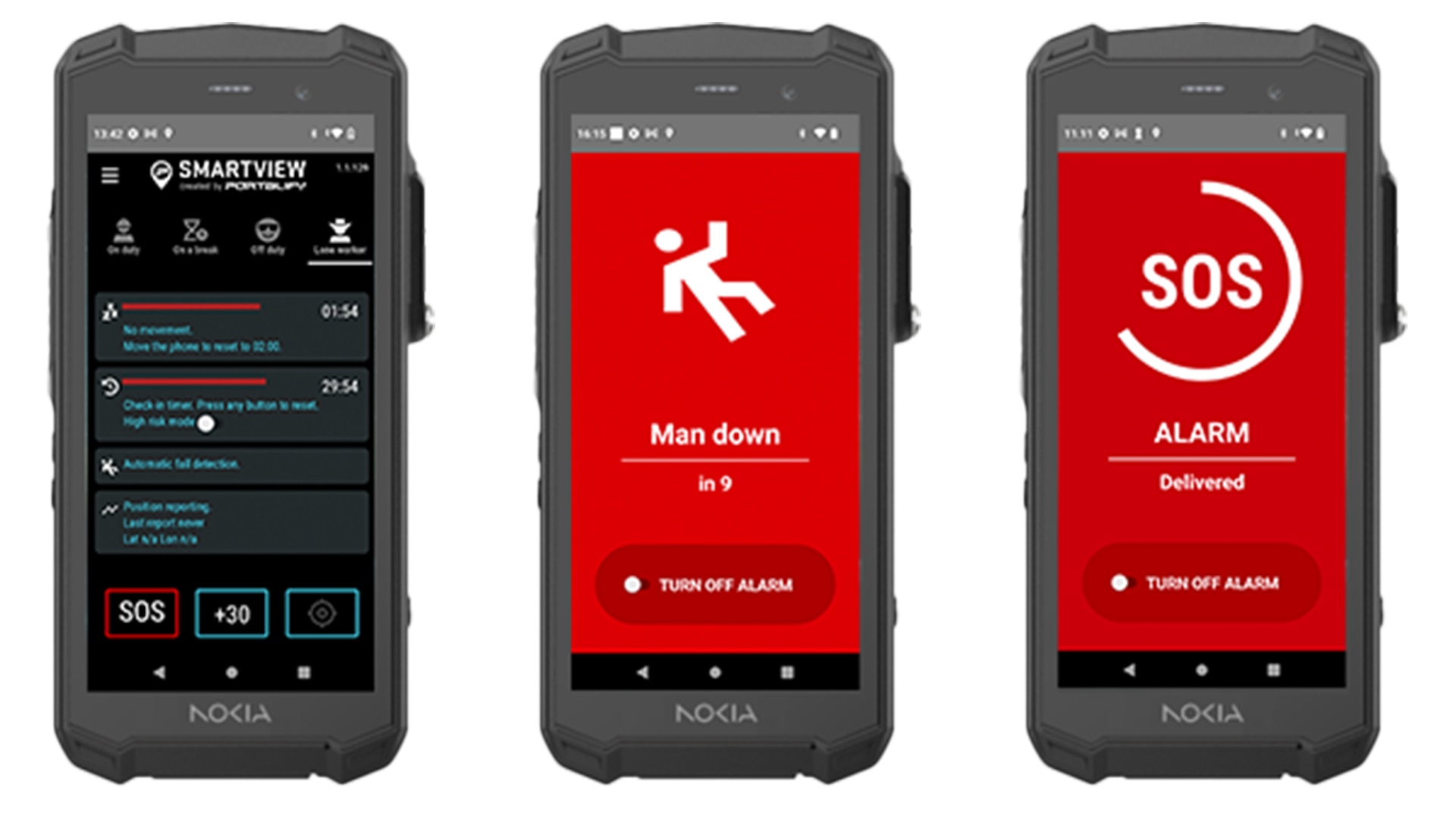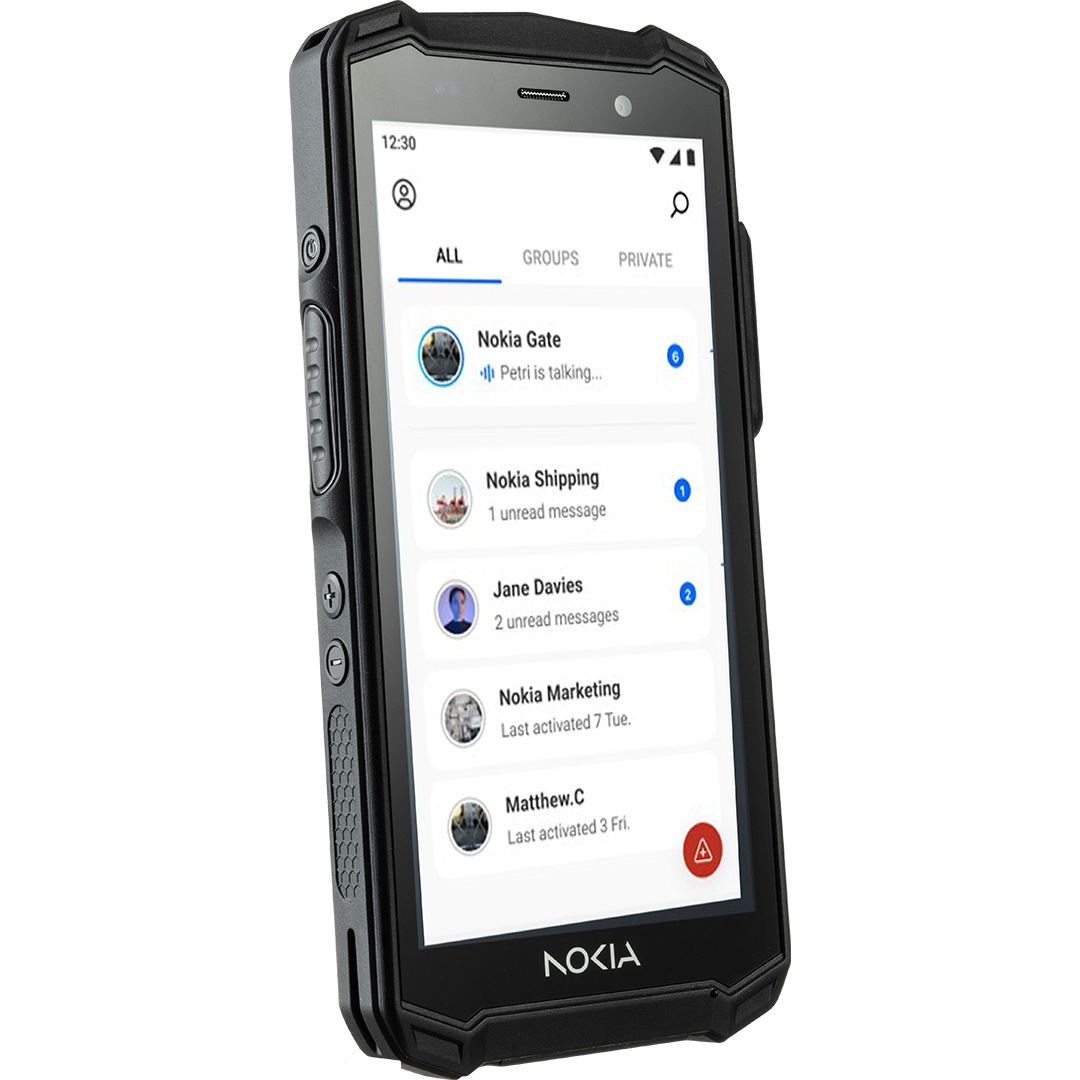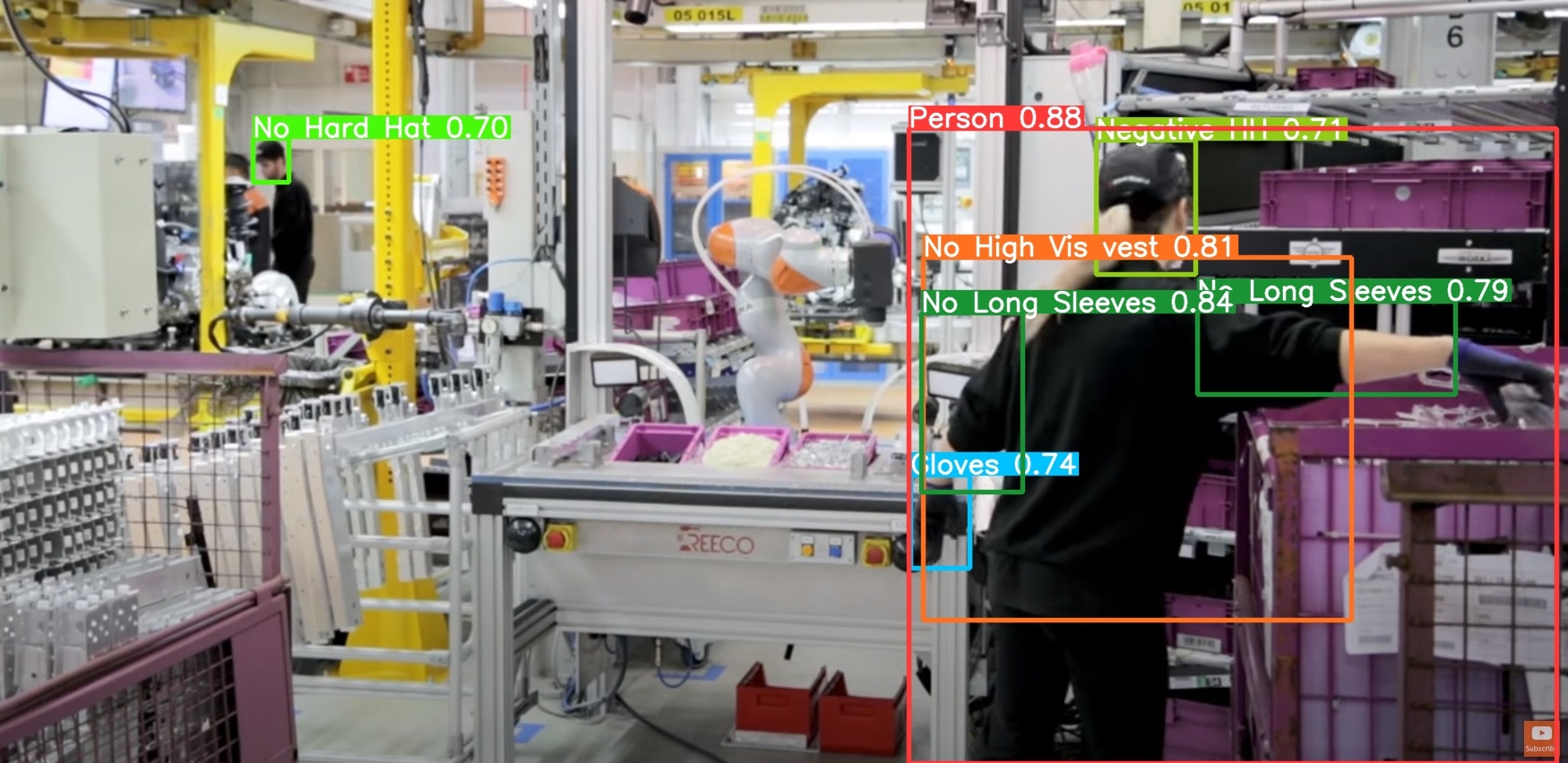
Nokia portfolio of industrial applications and devices
Select based on your needs/requirements
Featured applications and devices
Featured Devices
Portfolio
Product type
Application Categories
Device Categories
Usage
- Call and send messages
- Connect data
- Connect machines
- Connect workers
- (-) Deploy for devices
- Extend your reality (XR, VR)
- Find and track
- Improve efficiency
- (-) Improve enterprise security
- Improve device usability
- Improve productivity
- Improve worker safety
- Improve security
- Improve situational awareness
- Manage devices
- Monitor networks
- Support industrial protocols
- Use in hazardous environments
- Video communication / Visual data transmission
- Other
Industry Segments
Technologies
Certifications
-
Image

Nokia 360 5G & Wi-Fi cameras
Short descriptionThe Nokia 360° camera comes in three versions. Nokia 5G 360 Camera and Nokia 5G 360 Camera - Extreme Temperature connected over 5G cellular, with and without battery. And Nokia 360 Camera, which is connected over Wi-Fi and includes a battery.
All versions are industrial 360° cameras, which capture video and audio from full spherical view (360°x180°). The captured content can be stored in the SD card or streamed real-time to be processed and viewed with minimum latency.
The Nokia 5G 360 Camera provides 5G connectivity, high resolution and low latency 8K video stream, spatial audio, IP67 protection, and Nokia RXRM integration.
Manufacturer Manufacturer
Manufacturer
-
Image
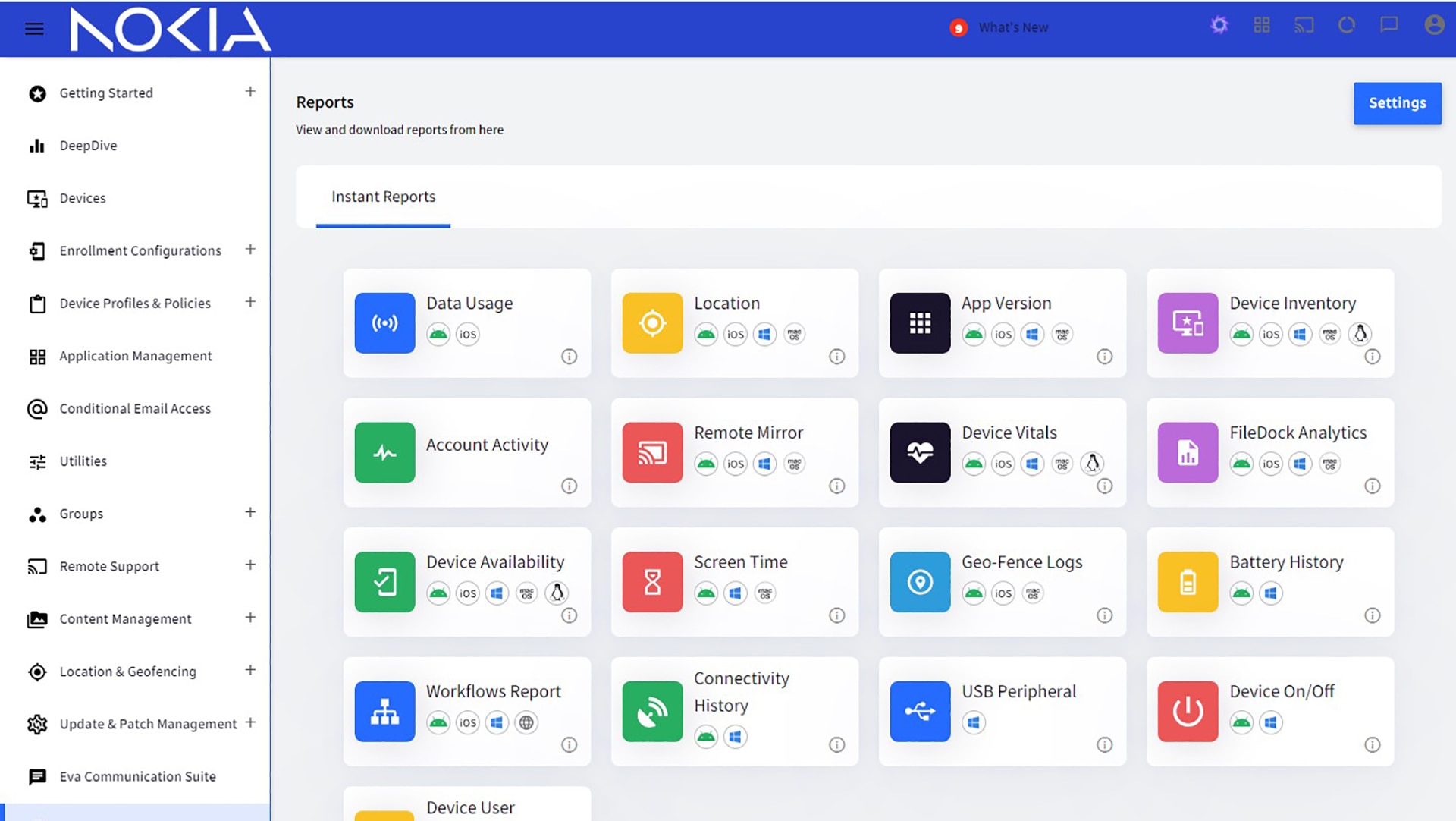
Nokia Industrial device management for smart devices
Short descriptionNokia Industrial device management - EMM (enterprise mobility management) provides an easy, secure way to deploy and administer Nokia Industrial phones. Manage your entire fleet of smart devices with an application that is built into Nokia private 4.9G/LTE and 5G wireless network solutions. Benefit from zero-touch and rapid onboarding of your Nokia Industrial phones.
Manufacturer Manufacturer
Manufacturer Image
Image
Nokia Industrial device management for smart devices
Short descriptionNokia Industrial device management - EMM (enterprise mobility management) provides an easy, secure way to deploy and administer Nokia Industrial phones. Manage your entire fleet of smart devices with an application that is built into Nokia private 4.9G/LTE and 5G wireless network solutions. Benefit from zero-touch and rapid onboarding of your Nokia Industrial phones.
-
Image
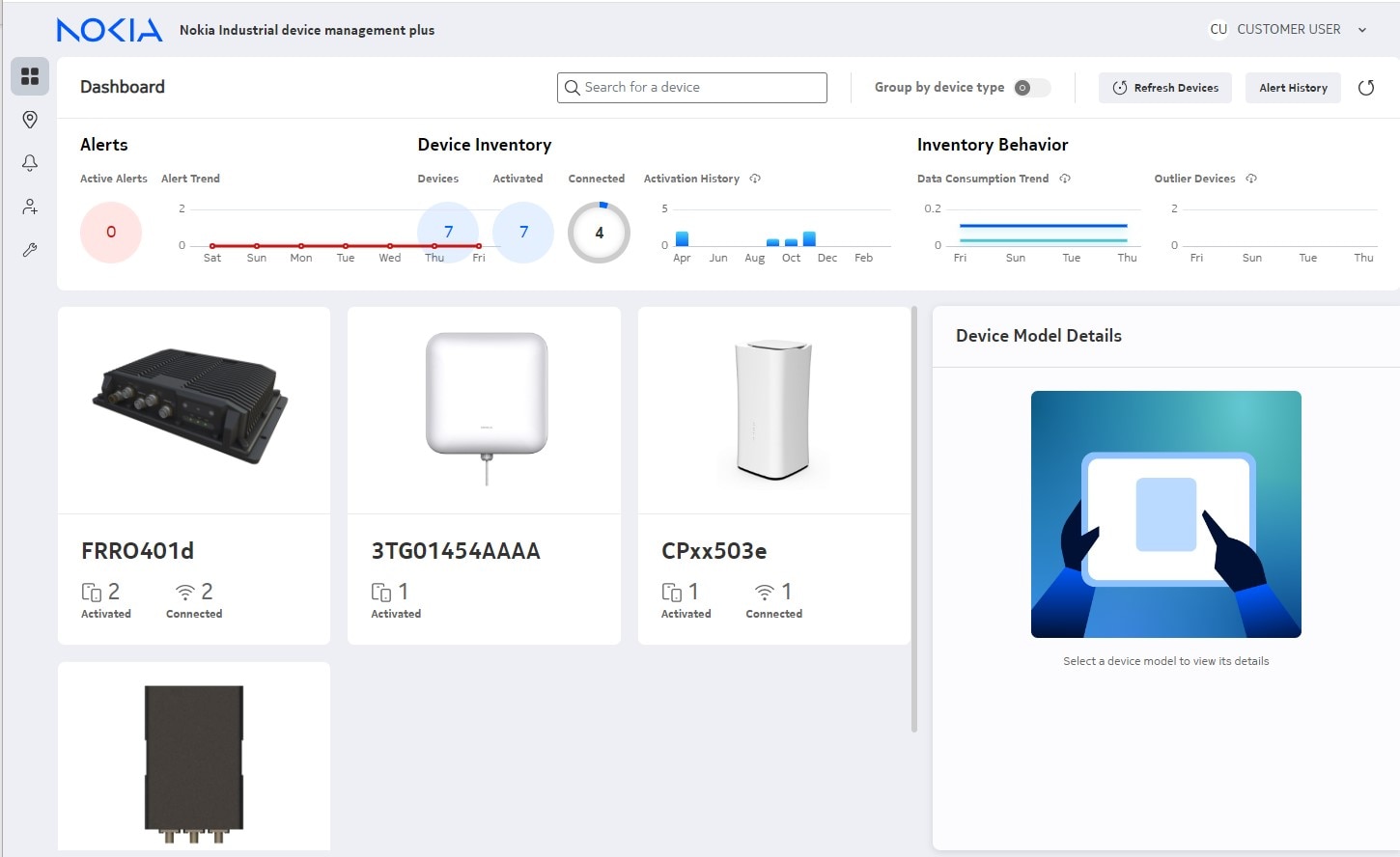
Nokia Industrial device management for IoT devices
Short descriptionNokia Industrial device management-IoT provides an easy, secure way to deploy and administer Nokia Industrial IoT devices. Manage your entire fleet of IoT devices with an application that is built into Nokia private 4.9G/LTE and 5G wireless network solutions. Benefit from zero-touch and rapid onboarding of your Nokia Industrial routers, dongles and other IoT devices. All Nokia Industrial IoT devices are built with software that allows them to automatically connect to Nokia Industrial device management eliminating the need to configure this in the field. Policies allow you to control the directives that are sent to the device upon connection.
Manufacturer Manufacturer
Manufacturer Image
Image
Nokia Industrial device management for IoT devices
Short descriptionNokia Industrial device management-IoT provides an easy, secure way to deploy and administer Nokia Industrial IoT devices. Manage your entire fleet of IoT devices with an application that is built into Nokia private 4.9G/LTE and 5G wireless network solutions. Benefit from zero-touch and rapid onboarding of your Nokia Industrial routers, dongles and other IoT devices. All Nokia Industrial IoT devices are built with software that allows them to automatically connect to Nokia Industrial device management eliminating the need to configure this in the field. Policies allow you to control the directives that are sent to the device upon connection.
-
Image
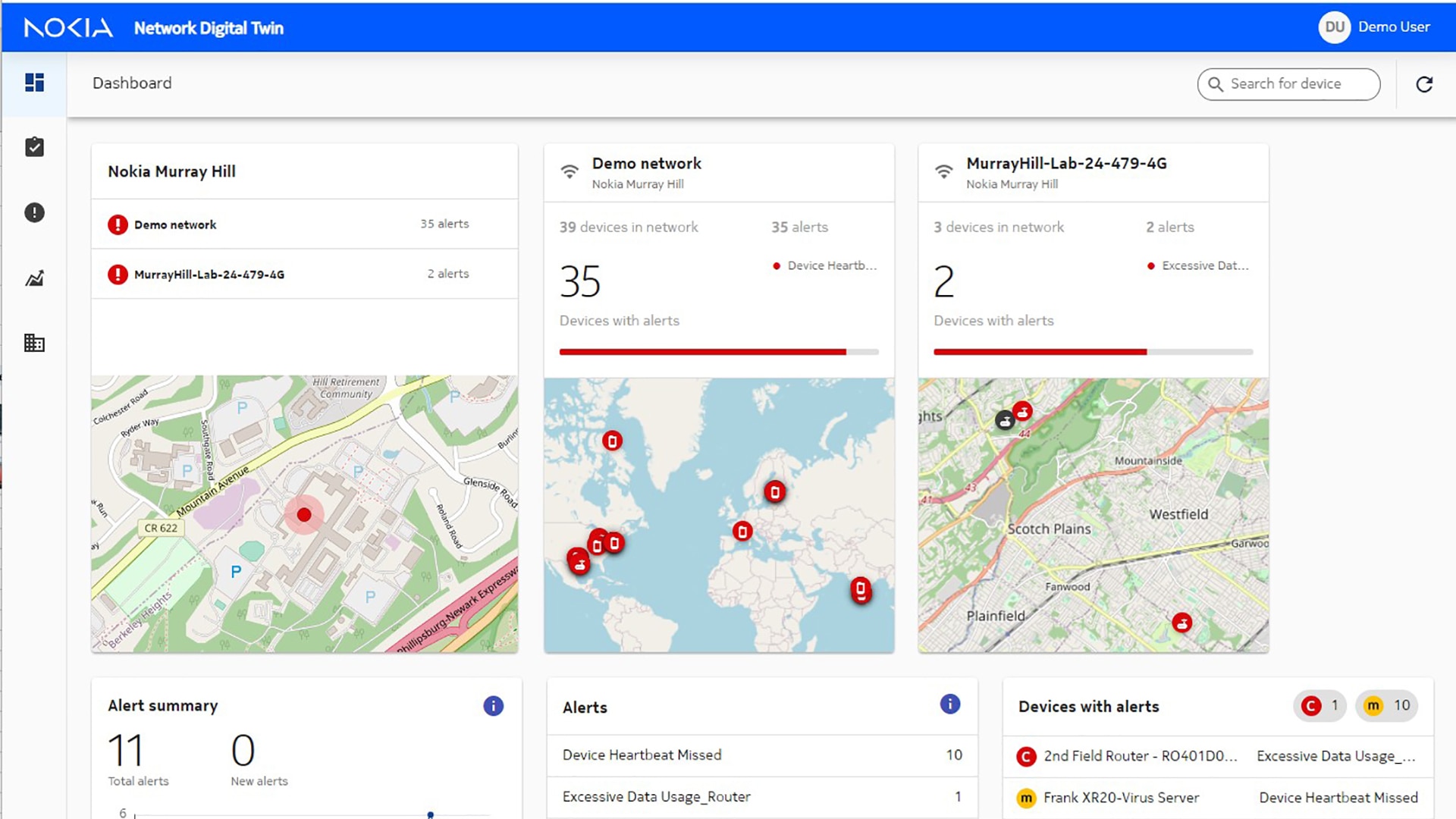
Nokia Network Digital Twin
Short descriptionNokia Network Digital Twin answers the key questions: “what happened?” and “what is happening?” on your devices as they send critical data over the network. You can monitor your network operations in near real time and receive alerts when a device is not performing as expected, allowing you to proactively take corrective actions. This helps you increase profitability by reducing disruptions to productivity.
Manufacturer Manufacturer
Manufacturer Image
Image
Nokia Network Digital Twin
Short descriptionNokia Network Digital Twin answers the key questions: “what happened?” and “what is happening?” on your devices as they send critical data over the network. You can monitor your network operations in near real time and receive alerts when a device is not performing as expected, allowing you to proactively take corrective actions. This helps you increase profitability by reducing disruptions to productivity.
-
Image

Nokia Team Comms
Short descriptionTeam communication for campus-wide usage
Get new integrated video and voice capabilities for reliable and secure campus-wide communications. Nokia Team Comms delivers business-critical push-to-talk voice, video and data communications allowing teams to collaborate on one-to-one and group calls, both indoors and outdoors, across any industrial campus without internet access. The application runs on Nokia MX Industrial Edge where data stays with you on prem.
Manufacturer Manufacturer
Manufacturer Image
Image
Nokia Team Comms
Short descriptionTeam communication for campus-wide usage
Get new integrated video and voice capabilities for reliable and secure campus-wide communications. Nokia Team Comms delivers business-critical push-to-talk voice, video and data communications allowing teams to collaborate on one-to-one and group calls, both indoors and outdoors, across any industrial campus without internet access. The application runs on Nokia MX Industrial Edge where data stays with you on prem.
-
Image

OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
Manufacturer Manufacturer
Manufacturer Image
Image
OneLayer
Short descriptionIIoT asset management and zero trust network access
OneLayer manages and classifies IIoT assets helping create inventory. It integrates with CMDB and policy enforcement and acts as a zero-trust access broker enforcing zero trust security principle for IIoT assets. It is directly integrated with FWs for automatic policy enforcement.
-
Image

Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
Manufacturer Manufacturer
Manufacturer Image
Image
Palo Alto Networks Next-Gen Firewalls
Short descriptionAdvanced Perimeter Security
Get advanced security powered by Palo Alto Networks. Palo Alto Networks software Next Generation Firewalls use AI and ML to prevent sophisticated cyber threats in the OT environment powered by Nokia MX Industrial Edge (MXIE), without adding physical hardware to the network. The comprehensive solution has industry-leading capabilities such as Advanced Threat Prevention, which blocks unknown command-and-control and exploit attempts in real time, Advanced WildFire, which stops highly evasive malware, DNS Security, which stops emerging DNS based attacks. Additionally, IoT/OT Security quickly profiles all OT, IT and IoT devices and assets, and protects them. This enables advanced security on both the IT and OT sides of the network to protect the entire organization with best-in-class security.
-
Image

Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Manufacturer Manufacturer
Manufacturer Image
Image
Redinent
Short descriptionIIoT asset discovery and vulnerability scanning
Redinent discovers IIoT assets via active scanning and helps create inventory. Probe response from IIoT devices is correlated with extensive IIoT specific vulnerability and threat intelligence data discovering vulnerabilities and ongoing threats. It generates alerts towards the SOC and reports about the findings.
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.